The Truss
Whitepaper
Version 3.0
Abstract
It is rare when something fundamentally alters how we interact with the world around us and each other. The personal computer, the cellphone, and 5G wireless communication are examples of how technology transformed the physical mediums we use to communicate and send information to each other. Blockchain technology, on the other hand, sets itself apart from these physical information mediums by transforming how we establish trust in information. It tackles profound questions surrounding our trust in the information we consume. It addresses concerns about consensus on the authenticity of specific events. It enables us to provide irrefutable proof of the occurrence of a particular event. In this remarkable way, blockchain paves the way for a paradigm shift in how we perceive and validate information, ushering in a new era of trust and transparency.
Blockchain up to this point has been largely focused on answering questions of trust from a financial perspective and leveraging the technology to enhance governance, privacy, and multi-signature authorization. In each use case, cryptologic functions are used to assert, without question, that a particular set of events are indeed true. This financial use case leads to the logical next step of applying blockchain technology in the information security industry. Blockchain operations share many parallels with security operations, including redundancy, transparency, privacy, and authentication. These fundamental aspects are deeply ingrained in both fields. This convergence prompts us to explore three critical questions:
-
Can we use the strengths of blockchain to store and provide security event data?
-
Can this include data developed and curated by a decentralized network of researchers to achieve validation or consensus?
-
Can we enable this security data to be sent directly to consumers in real-time to protect them from novel and viral threats?
We envision a world where peer-to-peer (P2P) communication of malware signatures, malicious Command and Control (C2) infrastructure, threat actor tactics, techniques, and procedures (TTPs), and security tools are streamed between the developer and the recipient. Where the transmission of security data is processed, purchased, and integrated in real time via smart contract automation. In such a world, when a threat actor launches a novel attack, within minutes every organization in the world has the security data required to prevent this attack from impacting their environment. To achieve this goal, we propose the development of a Decentralized Security (DeSec) global cyber immune system designed to combat the viral infections of cyber attacks.
This whitepaper presents a decentralized approach to providing relevant, simple, and economical security data. The concepts listed here present a new way to deliver, purchase, and retrieve security data that directly supports the research of and prevention of cyber attacks across the globe. Information security practitioners acknowledge the decentralized nature of attackers and how decentralized attack patterns present a technological and economic challenge to providing timely, actionable security data for organizations wanting to protect themselves. With this paper, we propose an alternative to centralized security vendors, one that takes a decentralized approach to combating cyber attacks.
Thanks,
The Truss Security Team
I. Cybersecurity Ecosystem
Cybersecurity Market
Security vendors are endeavoring to prevent and disrupt criminal cyber operations. They are working to develop detection and prevention mechanisms to ensure that organizations are protected from the worst of these cyber attacks. This has resulted in big business. The security industry is a $119 Billion dollar industry [17], has an expected growth rate of 8%, and employs more than 3.5 million people [4]. Every year cutting-edge technologies are showcased at trade shows and conferences, highlighting technologies designed to detect and prevent the latest attack techniques. Security experts are also seeing record-setting growth with an expected 31% growth between 2019 and 2029 [23]. Additionally, there are estimated to be 4.6 million total cybersecurity workers worldwide [24]. The battle between attackers and defenders has never looked quite as intense as it does today.
While the use of Artificial Intelligence (AI) holds promise for combating cyber attacks, it is only one of many responses that will be required to fight the pandemic. Reports show that a fully deployed AI learning model is only able to reduce the total dwell time of an attacker, post-breach, by 28 days [3]. AI thus reduces detection and remediation timing but at a much higher cost of operation.
Market Failure
To make ends meet, these organizations are forced to lean upon limited professional service time from their security vendors or they are forced to pay a Managed Security Service Provider (MSSP) to continually maintain their security tools. Organizations that have been compromised rely on security vendors to remediate the security incident, which adds an additional financial burden. As with all aspects in our modern economic culture, you get what you pay for, and most organizations are not able to afford the best MSSP, skilled security researcher, or the most comprehensive threat intelligence datasets.
The sharing of threat information is the lifeblood of the cybersecurity defense ecosystem, it allows for individual organizations to properly configure their security operation center tooling and allows for highly skilled threat analysts to accurately communicate threat information. This type of information is called Cyber Threat Intelligence (CTI). Threat intelligence is any information related to a threat that might help an organization proactively protect itself against a perceived threat or to detect the activities of a threat actor. Major types of threat intelligence include indicators, tactics, techniques, and procedures (TTPs), security alerts, threat intelligence reports, and tool configurations. Security operations rely on accurate and timely threat information to facilitate the monitoring of threats and to improve their defenses.
There are three requirements that must be met by security platforms to allow security operations to effectively respond to incidents.
- Security platforms must maintain relevant threat intelligence to remain secure. Relevant threat information is information that is both timely, trusted, and actionable.. In addition, organizations must rely on trusted threat data to avoid wasting resources tracking false indicators. There are many threat intelligence services that claim to be legitimate. Organizations should only use threat intelligence that has been reviewed and verified by trusted security professionals prior to their integration into security platforms.
- Security data must be simple. Organizations must be able to easily identify viral indicators and implement straightforward security measures in response to active cyber attacks. Maintaining a security tool that continually updates its rulesets to detect the latest attacks can dramatically improve an organization’s ability to survive that cyber attack. These rulesets often take a significant amount of work to implement and maintain. Oftentimes, too much for a medium-sized business to perform.
- Security products must be economical. Budget constraints affect every organization and only through the reduction of production costs can organizations afford to bring in the latest security technology to protect their environments. Medium-sized businesses directly feel this constraint as their entire yearly budget for security may only allow them to purchase the lowest tier of a dedicated threat intelligence platform or employ a security worker with limited practical security experience.
- Scenario #1 - Commercial security vendors can provide relevant, timely, and actionable threat information directly within their respective security operation tool that is simple to understand and implement. However, this oftentimes only comes with the purchase of premier security offerings, making these services too expensive for their security budget.
- Scenario #2 - Open source products such as MISP, OpenCTI, and many security GitHub repository tools can provide timely and actionable threat information that will assist security operations. Since they are free, they are also very economical to implement. However, these tools can be difficult to use, time-consuming to maintain.This requires a dedicated team member with advanced skills to properly implement them. Most mid-level organizations cannot provide this level of skilled work.
- Scenario #3 - Free threat intelligence lists can be simple to integrate into most security tools, reducing the burden on security personnel. But, many of the free threat intelligence lists contain old and irrelevant data, which may or may not have been verified by reputable sources. This security data thus delivers a false sense of security and leaves the medium-sized business slightly better off, but no where near sufficient in securing their environments
There is a significant demand for threat intelligence that supports the global mid-sized organization. This business demographic’s security needs are not being met by today's cybersecurity defense providers. As noted above there are traditionally two types of suppliers for security products: centralized commercial security providers and decentralized open source security researchers. The security products from centralized providers are high quality and easy to integrate, but they are oftentimes expensive and inaccessible to most organizations. The security products from decentralized security researchers are basically free, but they come from unverified sources, suffer from variable quality, and can be complex to integrate [16].
II. Decentralized Security
The immune system is nature's way of dealing with infections and diseases that enter the human body. It grows and adapts as we are exposed to foreign bodies like fungi, toxins, viruses, and bacteria, also called pathogens. The immune system maintains a network of sensors that sound the alarm when a pathogen is detected and in response creates antigens that our bodies remember forever to ensure they can quickly fight the infection should it return. Remarkably, instead of combatting the infection locally, the immune system provides the antigens to the entire body. This sharing of remediation information prevents a systemic infection from taking place within the body.
Today's modern and interconnected world is not all that dissimilar from a biological system. There are independent and diverse organizations and networks working in unison with the larger global society to maintain, support, and develop not only our modern lifestyle but the very ability to move forward and evolve. Arguably our society is still a nation-centric one, but we have begun to build global defense agencies such as Interpol and the World Health Organization which are capable of spreading information internationally regarding terrorism and pandemic-level events. However, today, there is a plague that is wreaking havoc across our interconnected world. A global pandemic that we have not been able to successfully combat or even significantly hamper. This pandemic is the Cyber Attack.
In a world where we can livestream any event to billions of users around the world, why do we still find ourselves in a situation where a cyber campaign can use the same type of attack to compromise hundreds of organizations over the course of several months and not be stopped? Is it not possible to build a global antibody armored against an attack's indicators of compromise (IOC) and deliver this to all organizations immediately? This type of global network immune system would undoubtedly protect potential victims, prevent criminal organizations from making large sums of money, and reduce the global threat of cyber attack pandemics.
Similar to how the immune system is able to globally deploy antigens to protect the whole body from a pathogen, the security industry needs to build a global network immune system to ensure that security infections taking place in one enterprise are rapidly disseminated to protect the global ecosystem. We should not live in a world where a single ransomware variant, or pandemic, is only fought locally and allowed to persist successfully for several months around the globe. Nor should we live in a world where 53% of all security breaches are not detected [11], or where the average dwell time of an attacker (the time from the initial breach until detection) is 207 days [7] plus another 70 days to contain the breach.
What is needed is a new, faster system for detecting, transporting, and deploying security-focused antigens to all global defenses to ensure they have correct and timely information to fight the infection. This system must not only respond to a singular infection but must also build the immunity response antigens to combat cyber infections on a global scale.
By pulling from nature, we are presented with a method to prevent wide-scale infections. Imagine, instead of a pathogen like a virus or bacteria, we are presented with a threat actor who has compromised a network. Imagine also, similar to how the immune system responds to a virus, the cyber immune system responds to the threat by deploying cyber antigens throughout the global network of interconnected organizations thus preventing infections in those networks. With the advancement of blockchain technology, it is now possible to achieve this imagined scenario: the creation of a global Decentralized Security (DeSec) cyber immune system.
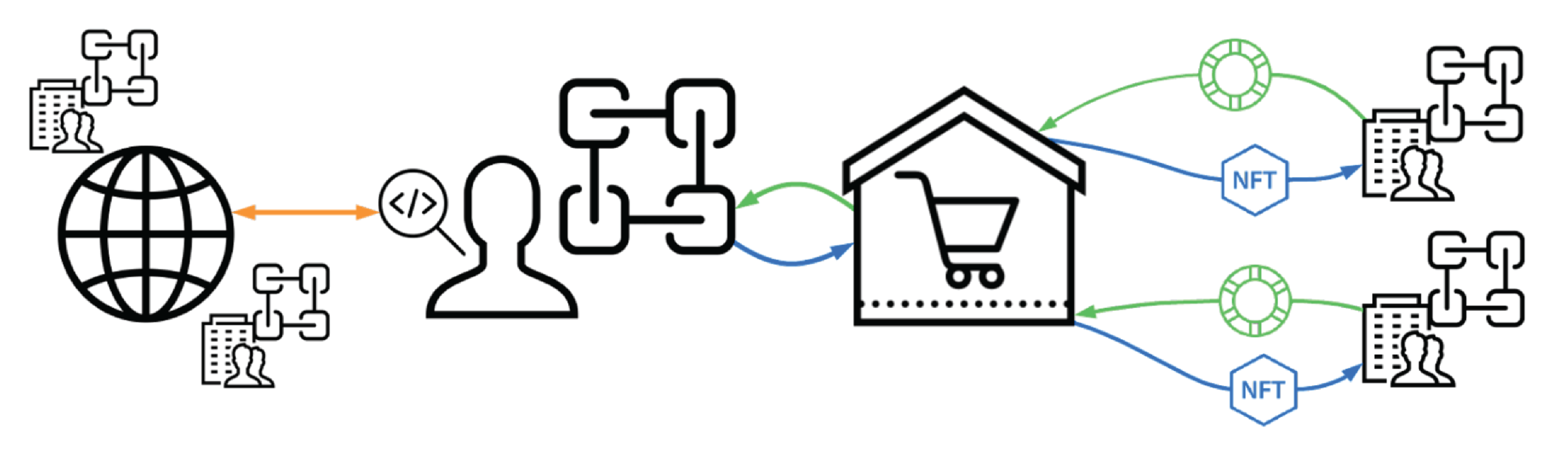
Truss Ecosystem
- On the right are the organizations that are the front line of attack and are often the first to recognize new attacks.
- On the left are the researchers who analyze organizational attack data and create the products that enable defenses against cyber attacks
- In the middle is the marketplace which serves as the hub for sharing data, creating security responses, and incentivizing participation from the community of researchers and organizations.
Truss Organizations
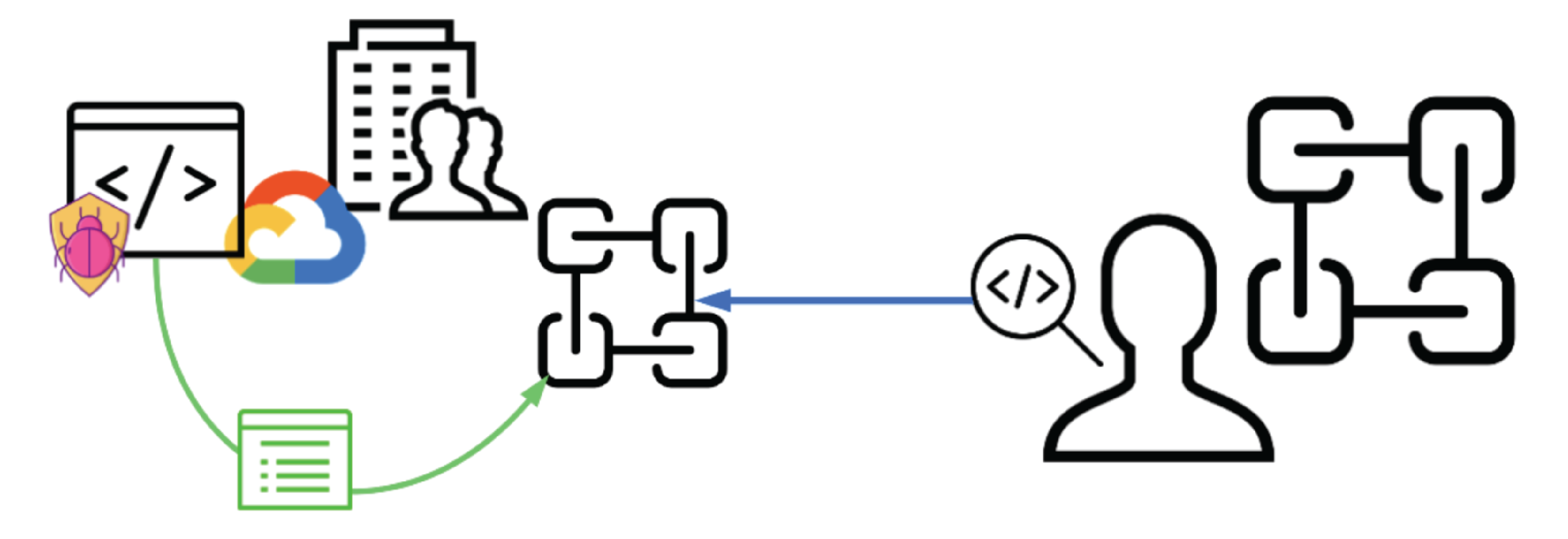
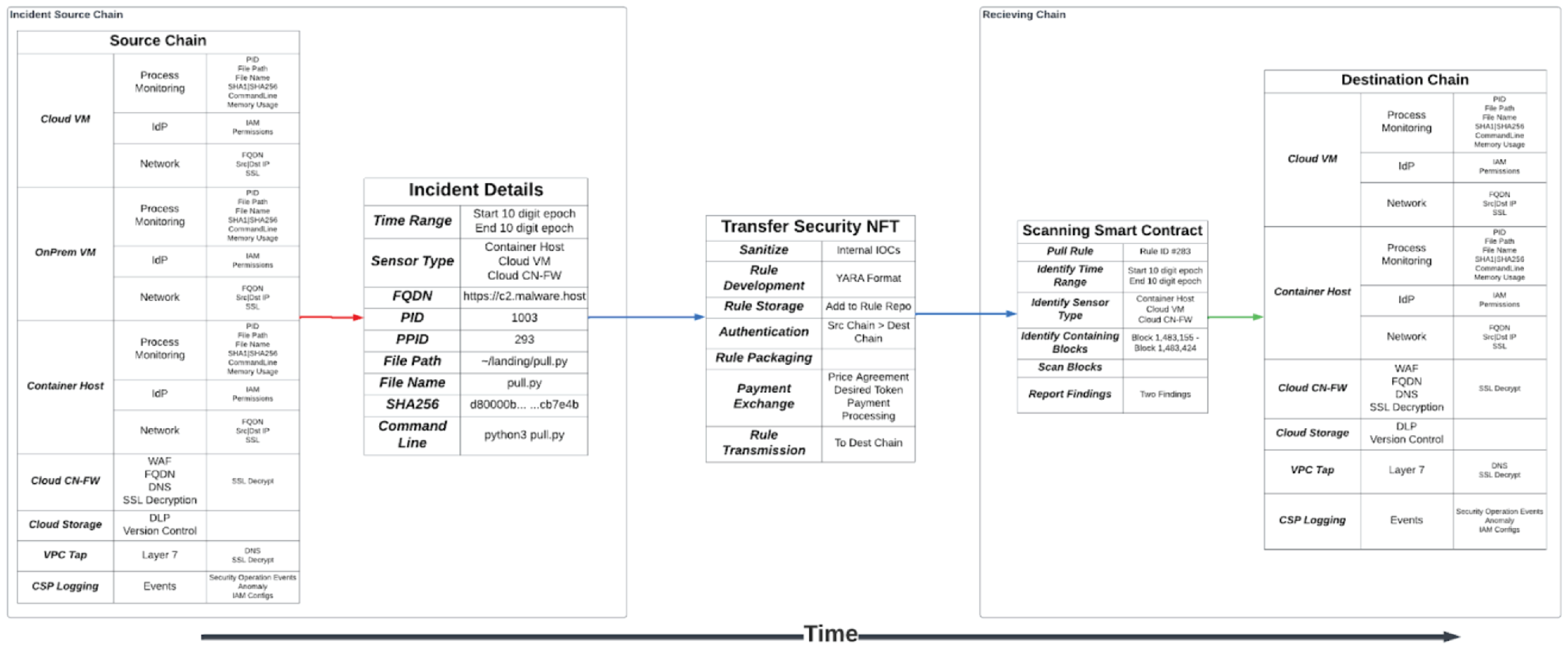
As illustrated in Figure 3, an organization records the security events taking place within its cloud environment. Should malware within a given container be identified, a list of the malware's IOCs is shared across the Truss network.
Truss Researchers
The Truss platform provides an avenue that enables independent security analysts to get compensated for sharing CTI. Analysts who uncover cyber threats and publish their findings are able to cryptographically sign their CTI and post it to the blockchain. Organizations subscribing to receive CTI each pay a fee to access the data and a portion of the fee goes back to the analyst. By enabling this point-to-point connection between independent analysts and organizations, the Truss ecosystem promotes a positive feedback loop that encourages more analysts to contribute, which then encourages more organizations to participate. The ultimate goal is to untether security data production from centralized organizations and unleash the potential of the decentralized community of analysts.
In addition to sharing security event information directly, the Truss platform also provides an avenue for security practitioners to investigate and hunt for security events across the global Truss network, effectively removing enterprise-focused security vendors as the sole proprietors of large-scale security-related information. As Figure 4 illustrates, analysts will have the opportunity to request query capabilities into select organizations in order to review the security logs from that organization.
The tokenomics of the Truss ecosystem actively works to incentivize all participants within the ecosystem to work together to produce high-quality and high-fidelity products that benefit each participant within the ecosystem. The more trustworthy the analyst, the more likely organizations will be incentivized to allow them access to their data. The more an organization opens its data to analysts, the more opportunities the organization has to help protect the larger ecosystem as well as the more opportunities they have to economically benefit from their data.
Truss Marketplace
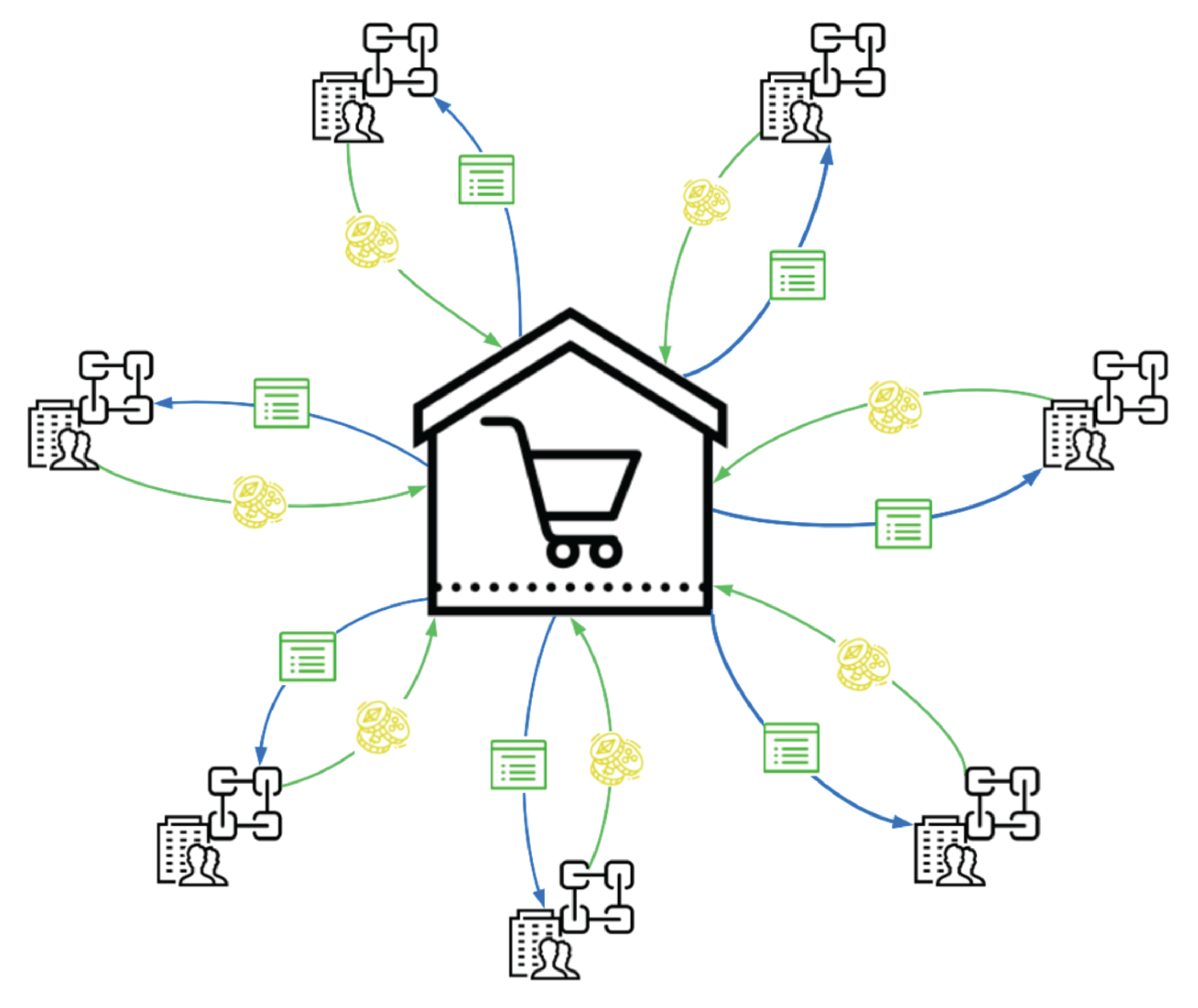
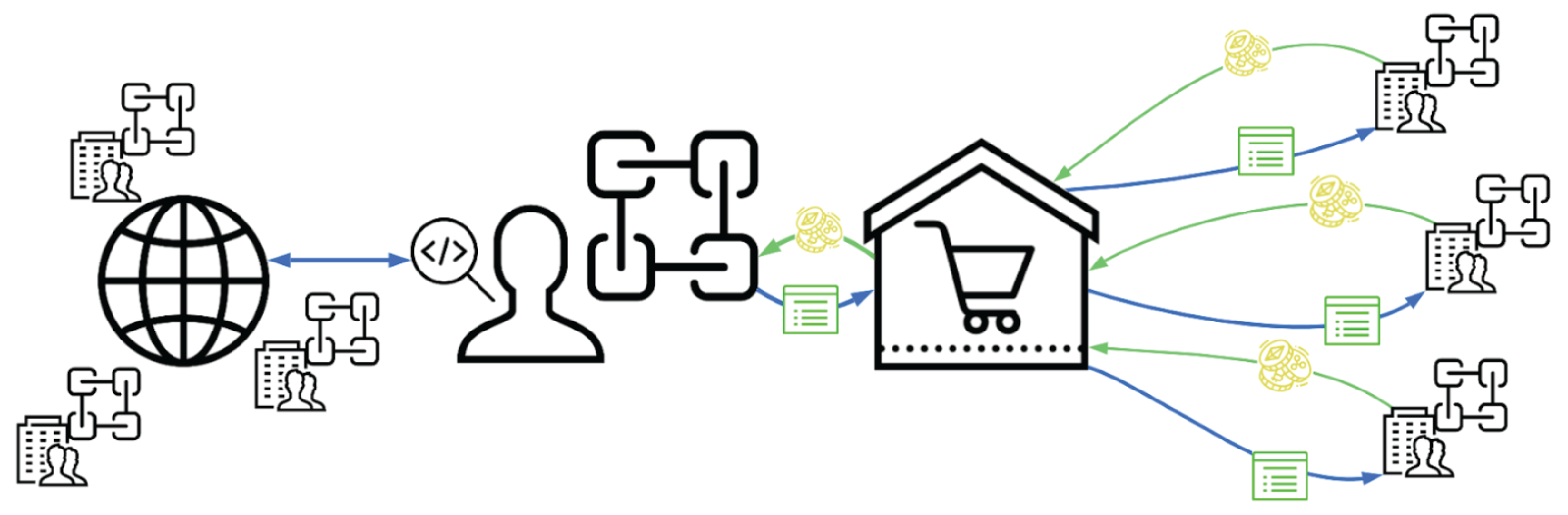
In addition to providing the infrastructure for collecting and disseminating attack data, there must also be incentives for security practitioners and organizations to contribute their time and data. Subsequently, the Truss ecosystem provides an avenue for analysts to sell their protection products to a global audience through the development of security marketplaces. Using a public blockchain to share security events, and allowing analysts to scan and build protections based on data from the blockchain fosters the creation of a self-sufficient ecosystem of security knowledge, skills, resources, and protections. Organizations and individuals alike will be free to integrate and sell purpose-built collections of security detections directly to end-users reducing the cost of security protections while simultaneously encouraging advanced research.
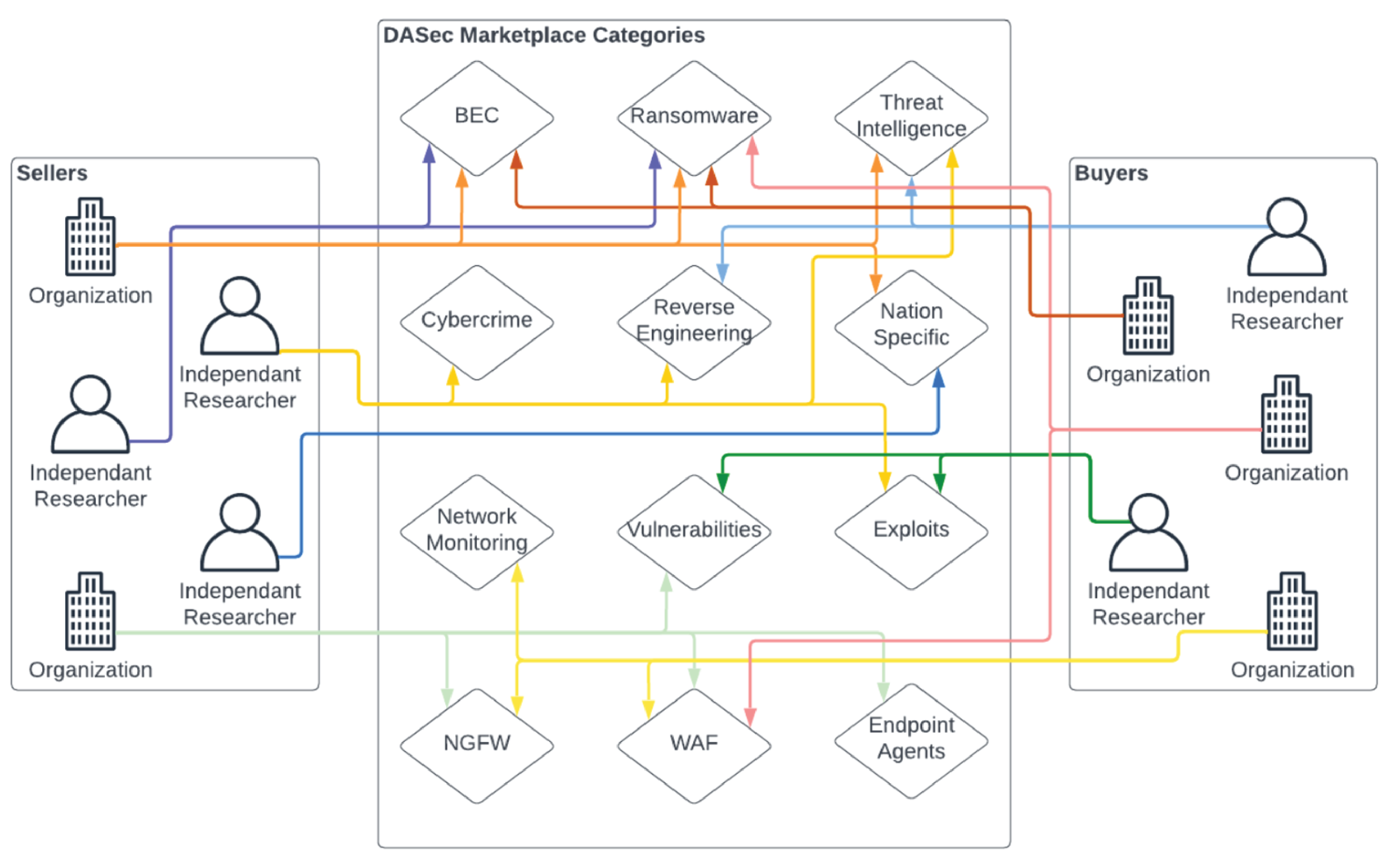
Any Truss entity can be a consumer, seller, and creator within the Truss ecosystem. The Truss ecosystem will assist Truss entities to buy and sell their security products through a Truss Marketplace. The Truss Marketplace will be designed to facilitate access and searchability to enable users to quickly find, access, and implement the security products they need to protect their environment. The Truss Marketplace will provide sellers with virtual counter space to present their products in a user-friendly and easily navigable method.
Truss entities can earn proceeds by providing research, detections, and remediations for the latest security risks facing global networks and computational endpoints to the Truss Marketplace. These security products can then be purchased by any other Truss entity.
A Truss Marketplace should be designed with ease of use in mind. Each security product will be tagged with common security industry identifiers allowing consumers to quickly identify the specific type of product they are interested in buying. See Figure 6, for an example of how sellers and buyers will use the marketplace's organization.
Through the marketplace, any Truss entity can buy security products directly from the creators of that product. This direct approach should reduce the cost and increase the availability of security solutions. The Truss ecosystem also provides an avenue toward profitability for a large enterprise-level Truss entity's security team. By allowing these security teams to sell their security knowledge and expertise, the enterprise security team can transition into a profitable investment, instead of the ever-necessary and ever-rising cost of doing business.
III. Decentralized Architecture
On-Chain Innovation
The Truss platform also promotes economic innovation wherein security analysts and organizations are able to explore different models for packaging and selling threat data and products. For example, one analyst may want to charge a premium for their product because it addresses a complex attack. Another analyst may want to charge a minimal amount and try to sell on volume. Some analysts may want to include a fee that creates an automated "marketing bounty" to use on a specific product. Some analysts may want to allocate a minimal amount to pay for community sales reps while others may want to give away much more of their margin to encourage the sales team.
One of the key characteristics of the Truss platform is its openness and accessibility. It allows anyone to participate, create their own security products and tools, and engage in transactions with other participants. This openness promotes transparency, inclusivity, and equal opportunity for all users, fostering a dynamic Truss ecosystem. In turn, this empowers security analysts and organizations to create and execute programmable agreements, automate processes, and build decentralized applications that can disrupt the traditional threat intelligence supply chain and enable new forms of digital interactions to combat cyber attacks.
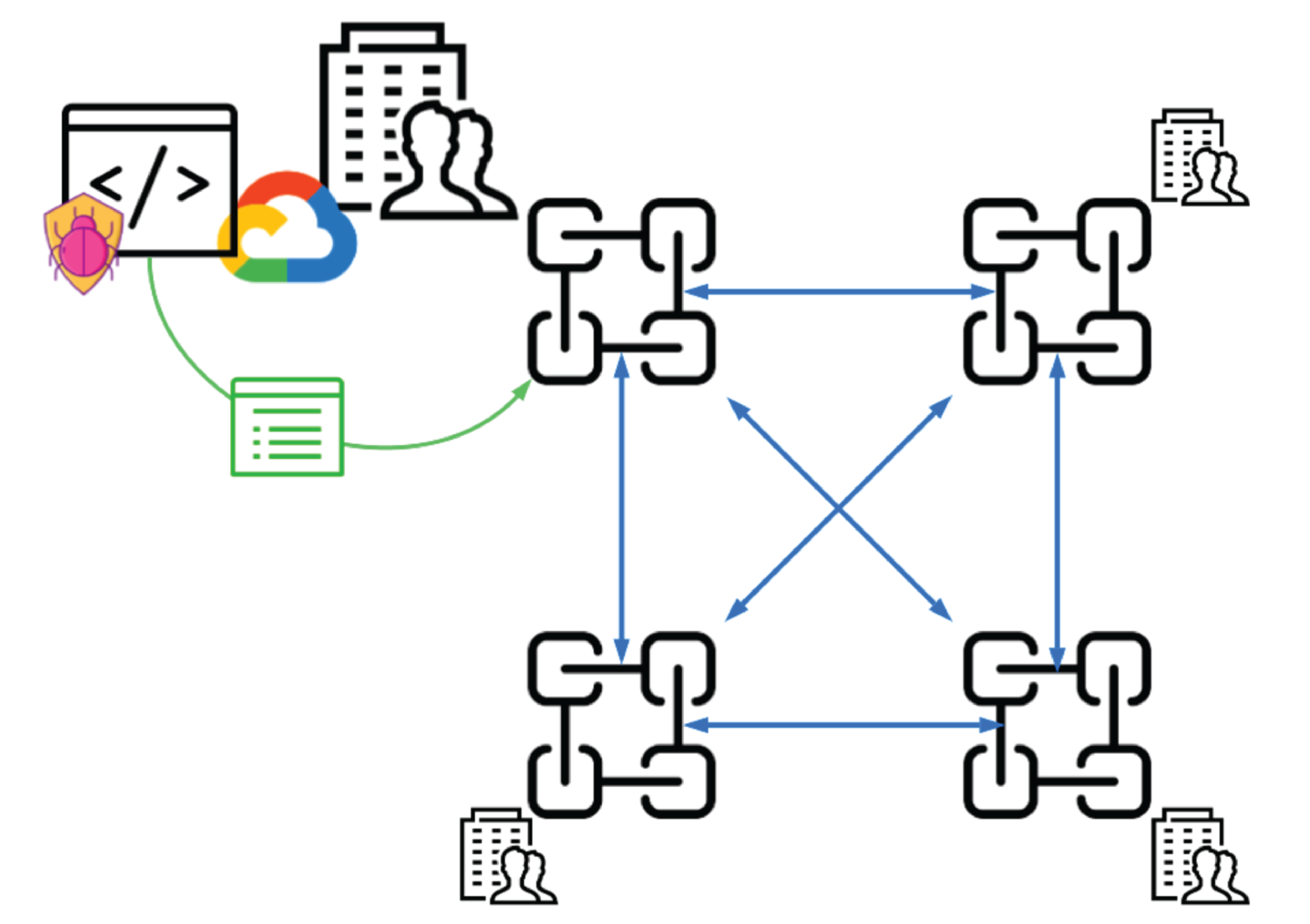
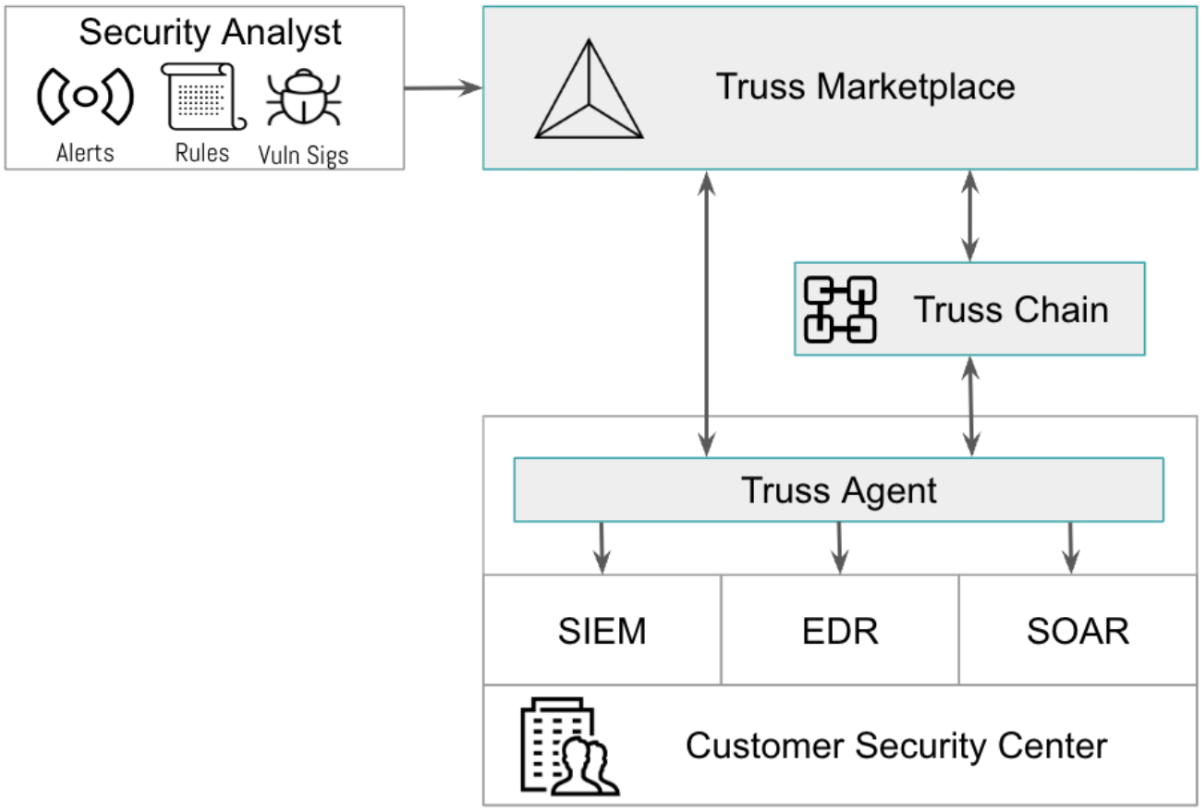
There are three components to the Truss architecture (Figure 8): the Truss marketplace, the Truss chain, and the Truss agent. The marketplace was described earlier in the whitepaper. The remainder of this section explores the Truss Blockchain and Truss Agent.
Truss Blockchain
A decentralized public ledger architecture has several benefits that make it an effective solution for meeting the requirements of a DeSec system:
- Global reach: Blockchains operate on a decentralized network, which means there is no central authority controlling or managing the data. This decentralized nature eliminates the need for intermediaries and allows for direct peer-to-peer transactions. This feature is particularly advantageous for organizations and analysts who may not have access to commercial security SaaS platforms.
- Relevant and timely intelligence: While centralized security organizations have shown that they can create relevant and timely threat intelligence data, their ability to scale is dependent upon the number of security analysts that have been hired by the organization. An open blockchain platform is able to scale to any number of security analysts. In addition, as soon as a threat is discovered and threat intelligence is posted and validated on the blockchain, mitigation data for that threat is immediately available to every organization and security consultant. This enables the near-instantaneous transfer of threat intelligence and eliminates delays associated with corporate bureaucracies or limits on political cross-border transactions.
- Cost-effective: Centralized security providers expend resources to collect, store, and analyze security data. These providers are incentivized to collect as much security data from their customers as possible in order to build protections. However, with an ever-expanding set of resources, they are forced to acquire new customers to help keep costs low for their customer base and the resource cost versus return cycle continues to spiral. [18]. By using a blockchain and eliminating the need for intermediaries, the suppliers and consumers of threat intelligence can directly transact with one another, reducing time and costs.
- Security: Blockchain technology provides a high level of security and trust in transactions. The data stored on the blockchain is encrypted and distributed across multiple nodes in the network, making it highly resistant to tampering and fraud. This feature is crucial when dealing with global customers as it helps establish trust in the transactions and ensures the integrity of the information being shared.
- Transparency and trust: Blockchain offers transparency by maintaining an immutable and auditable record of all transactions. Every participant in the blockchain network can access the same information, creating a transparent and shared ledger. In the context of the creation and transfer of threat intelligence, this transparency is beneficial for global customers as it allows them to verify the provenance of the data used to develop the CTI making it easier to establish trust in the CTI.
- Incentivization: A blockchain token presents a straightforward way to offer incentives to developers, organizations, and analysts who contribute to the Truss ecosystem. These incentives can come from fees paid into the ecosystem by other participants, or they can be more direct in the form of token grants, bounties, funding for building applications, or providing other valuable services.
Public Chain
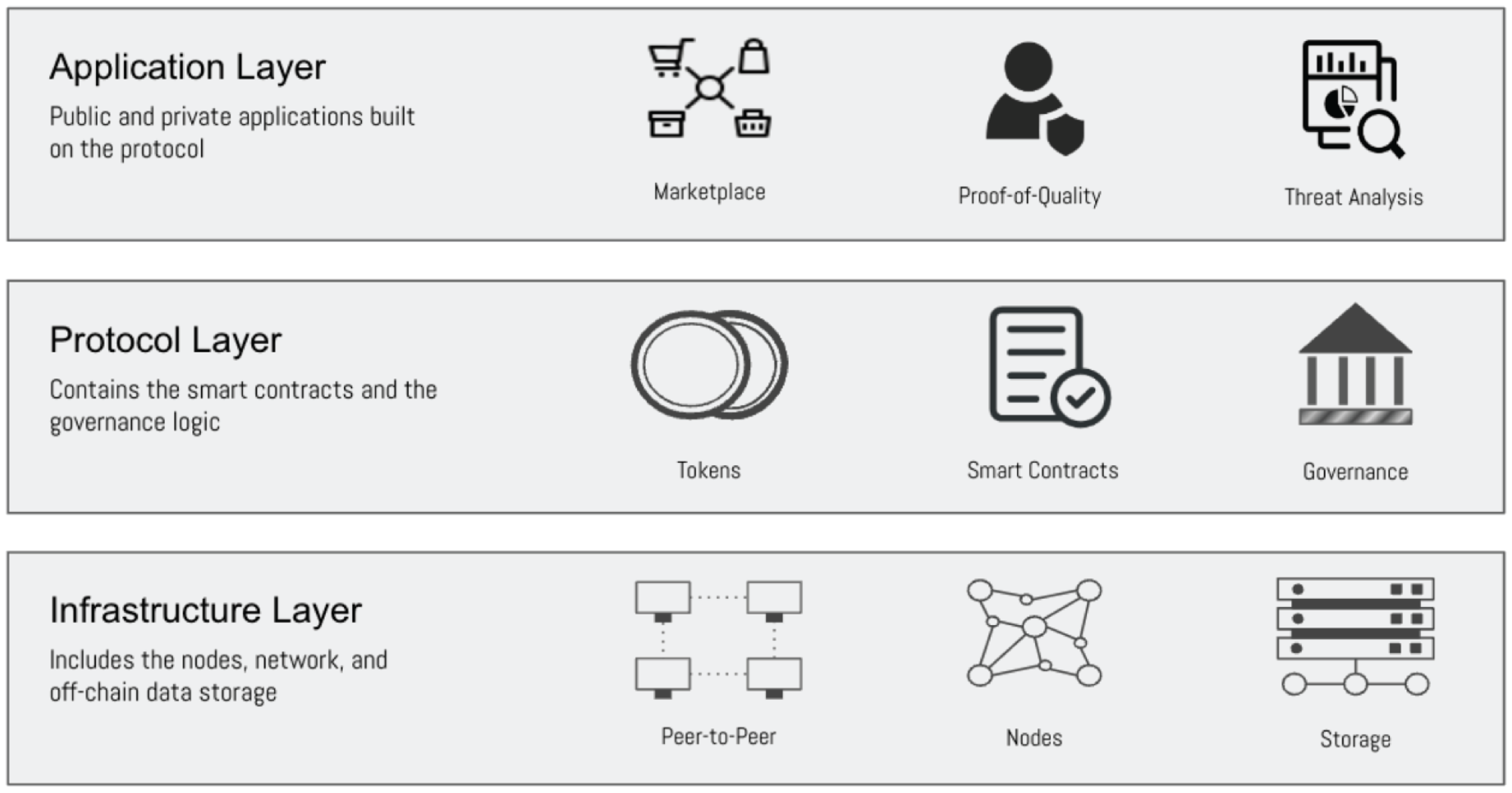
The protocol layer of a blockchain encompasses the rules, algorithms, and protocols that govern the operation and behavior of the blockchain network. It includes elements such as the consensus algorithm, block creation and validation rules, cryptographic algorithms, and transaction validation protocols. The protocol layer also holds the smart contracts that define the rules, terms, and conditions of interactions between Truss entities.
The infrastructure layer forms the foundation of the blockchain network. It includes the underlying hardware and network components that enable the functioning of the blockchain. This layer encompasses the physical infrastructure, such as servers, nodes, and data centers, as well as the networking infrastructure that facilitates communication and data transmission between the nodes in the network.
At the infrastructure layer, blockchain nodes are deployed, which are responsible for maintaining a copy of the blockchain's distributed ledger, participating in the consensus mechanism, and validating transactions. The infrastructure layer ensures the availability, reliability, and scalability of the blockchain network.
While it is possible to imagine Truss use cases, such as highly specific requirements or unique consensus mechanisms, that would require building a domain-optimized layer 1 infrastructure, deploying contracts to an existing layer 1 blockchain offers significant advantages in terms of security, reliability, network effects, interoperability, developer support, cost efficiency, and user trust.
The Truss API
The Truss blockchain API will support organizations and security analysts wanting to access security event information and security products. The API exposes a variety of endpoints or methods that developers can use to interact with the blockchain network. These endpoints include functions such as submitting transactions, validating threat intelligence information, and querying account balances.
Similarly, the Truss marketplace API is available for peer-to-peer interaction with marketplace functionality. Threat intelligence feeds, access to the latest security product information, and the purchasing of products and tools is all available via the marketplace API. It is expected that agent applications running within an organization’s network will communicate directly with the chain and marketplace APIs allowing organizations to customize where security information is sent to.
The Truss Security Agent (TSA) is a pivotal component of the Truss platform. It acts as an intermediary, linking the organization's SOC to a wide array of security information and products available on the Truss Marketplace. Through the software agent, organizations can download security threat intelligence and threat alerts, sourced from trusted entities and experts worldwide. This marketplace of security products ensures that organizations can access tailored and up-to-date information, specific to their industry, geography, and operational context.
The TSA enhances the capabilities of the organization's cybersecurity infrastructure by complementing existing Endpoint Detection and Response (EDR), Security Information and Event Management (SIEM), and Security Orchestration, Automation, and Response (SOAR) tools. By incorporating blockchain-based threat intelligence, the TSA enriches the data available to these tools, providing a more comprehensive view of the threat landscape. This augmentation bolsters the organization's ability to identify, mitigate, and respond to threats more effectively and efficiently.
IV. Incentivization Model
The Truss platform supports the participation of the global security community and encourages adaptability and innovation through its token-based incentivization model. It incentivizes participation by distributing the value accrued by developing and purchasing security products and tools to those contributing to the protocol.
A token-based incentivization model creates an environment where users can experiment with the design and distribution of security products in such a way that encourages risk-taking and creativity. In addition, because the Truss protocol is available to anyone with access to a node, it becomes possible to tap into the wisdom and expertise of a broad and diverse group of security experts.
The Truss token
The Truss token will be used as the principal unit of exchange within the Truss ecosystem and will be considered a Utility Token [12]. In the context of blockchain, a token providing a utility refers to its ability to have functional value or usefulness within a specific ecosystem or network. The Truss token will be used to facilitate the economic requirements of scanning a public blockchain, purchasing security products from the Truss Marketplace, purchasing a seller's space within the marketplace, and paying gas fees for writing to the layer 1 blockchain. In addition to the economic functions of the Truss token, it will also incentivize participants of the Truss ecosystem to share information about security events taking place within their computational environments.The Truss public chain will implement a fee-sharing token economic model that collects fees for payment and distributes them to analysts, developers, and other Truss entities. This model is useful in blockchain-based ecosystems to incentivize participation and contributions from various stakeholders.
The following is a simplified explanation of how the Truss token economic model will work:
- Token Creation: A native Truss token will be created for the platform. This token serves as the medium of exchange and represents value within the system. For example, within the Truss Security ecosystem, the Truss Token will be created to fulfill the token objectives.
- Fee Collection: Whenever on-chain transactions or payments occur, a fee is charged. These fees can be a percentage, or fixed amount, of the transaction value.
- Fee Distribution: The fees will be distributed among different participants according to predefined rules. These rules can vary depending on the product or service being offered. For example, the fees might be divided among security product publishers, analysts, data sources, the Truss marketplace, the Truss foundation, and other Truss entities.
Token Utility
Publishing and Purchasing Security Products and Tools: Each security product transfer will take place through the exchange of Truss Tokens between the seller and purchaser. The seller will sell the security product, which the purchaser will then use Truss Token to purchase.
Access to Security Services: Utility tokens can grant holders access to specific services or features within a decentralized application or platform. For example, a token might be required to access premium content, use certain functionalities, or participate in voting or governance mechanisms. Sellers may also put up a contract for the use of their services, such as Pentesting operations, Incident Response operations, Security analytics, or even architectural or security consulting services. Each of the services made available will use the Truss Token to facilitate the service agreement.
Access to Organizational Security Data: When organizations open their security events to the public, they open the door to receiving Truss token rewards for the use of their data. This public data is available to a subset of users of the Truss ecosystem and can be used to create security products that can be sold on the Truss Marketplace.
Truss Marketplace Transactions: The majority of purchased security products will be performed within the Truss Marketplace. While the Truss chain is public and the direct sale of security products between Truss entities can take place, the Truss marketplace will provide ease of access and product support allowing users to quickly discover trending security products and interact with peers to build stronger relationships. The Truss Marketplace will provide a centralized location for all security products to aid in the ease of discovery of critical security events. The Truss Marketplace will also provide the service of marketing and providing real estate for analysts and security vendors to generate revenue for their security products.
Industry Information: The Truss Marketplace will provide a number of beneficial services for the industry at large, including hosting a Top 10 Trending Security Product listing which will be continually updated to show the most pressing or time-sensitive security products requested and purchased by the Marketplace clientele. The Truss Marketplace will also maintain a Top Security incident board, highlighting the latest industry news and breach alert notifications to ensure that users are up to date on the latest security incidents as they occur. Additionally, the Truss Marketplace will maintain analytic functionalities to pair organizations with new security products. When new products are developed, organizations will receive customizable notifications of potential new security mitigations being made available through the marketplace.
Token Distribution
There are several methods that will be used to facilitate the distribution of Truss tokens.
Genesis Token Allocation
Advisors and Partners: As a community-driving protocol, Truss will seek guidance from industry experts, advisors, and strategic partners who contribute their knowledge, experience, and networks. These individuals or entities may receive a portion of the token allocation as compensation for their support and contributions to the project.
Early Investors/Seed Funding: Investors provide capital at an early stage and bear the risk associated with the project's success and help kickstart its development. In exchange for this risk, early investors may receive a portion of the Genesis token pool.
Community and Airdrops: To foster community engagement and wider adoption, Truss will reserve a portion of the initial token supply for distribution to the community.
Marketing and Development: A portion of the token supply may be allocated to marketing initiatives, including promotional activities, partnerships, and exchange listings. This allocation helps create awareness, drive adoption, and support the ongoing development of the protocol.
Token Purchase
Token Exchange
Governance and Voting
A key requirement of a token-based blockchain is the establishment of a governance model for the token and the protocol. There are several goals that need to be addressed by the governance model:
Protocol Evolution: Blockchain protocols are not static and may need to evolve over time to address security vulnerabilities, scale the network, introduce new features, or adapt to changing user needs. A governance model provides a mechanism for proposing, discussing, and implementing protocol upgrades or changes. It allows stakeholders to contribute to the decision-making process and reach consensus on these modifications.
Community Engagement: Tokens are often associated with vibrant communities of developers, users, and enthusiasts. A governance model fosters community engagement by involving token holders in important decisions. It gives them a sense of ownership and empowers them to actively participate in shaping the future of the blockchain ecosystem. This engagement can lead to a better alignment of interests and increased commitment to the network's success.
Conflict Resolution: Disagreements and conflicts can arise within blockchain communities, such as debates over proposed upgrades or the allocation of resources. A governance model provides a structured framework to address and resolve these conflicts in a transparent and democratic manner. It establishes rules and processes for decision-making, ensuring that conflicts are resolved fairly and efficiently.
Long-Term Sustainability: Tokens are often tied to the economic aspects of a blockchain ecosystem. A governance model helps ensure the long-term sustainability of the token and the network by addressing economic factors such as inflation, token supply, token distribution, and economic incentives. It enables stakeholders to make informed decisions about these economic parameters and maintain the stability and viability of the token and its ecosystem.
V. Future Vision
As the Truss ecosystem evolves, it can also support the sharing of anonymized organizational log data that can be used by security analysts to support the creation of threat intelligence. In this case, there would also be a private component of the Truss ecosystem that provides for secure storage of organizational security data. This necessitates the creation of a hybrid blockchain, where private organizations will maintain a private blockchain of their own internal security events, but simultaneously allow the organization to share parts of their private data on a public blockchain that is available to all users of the Truss ecosystem.
This section explores the introduction of private blockchains into the Truss ecosystem with the goal of enabling real-time sharing of organizational event logs to the community of Truss analysts.
Hybrid Blockchain
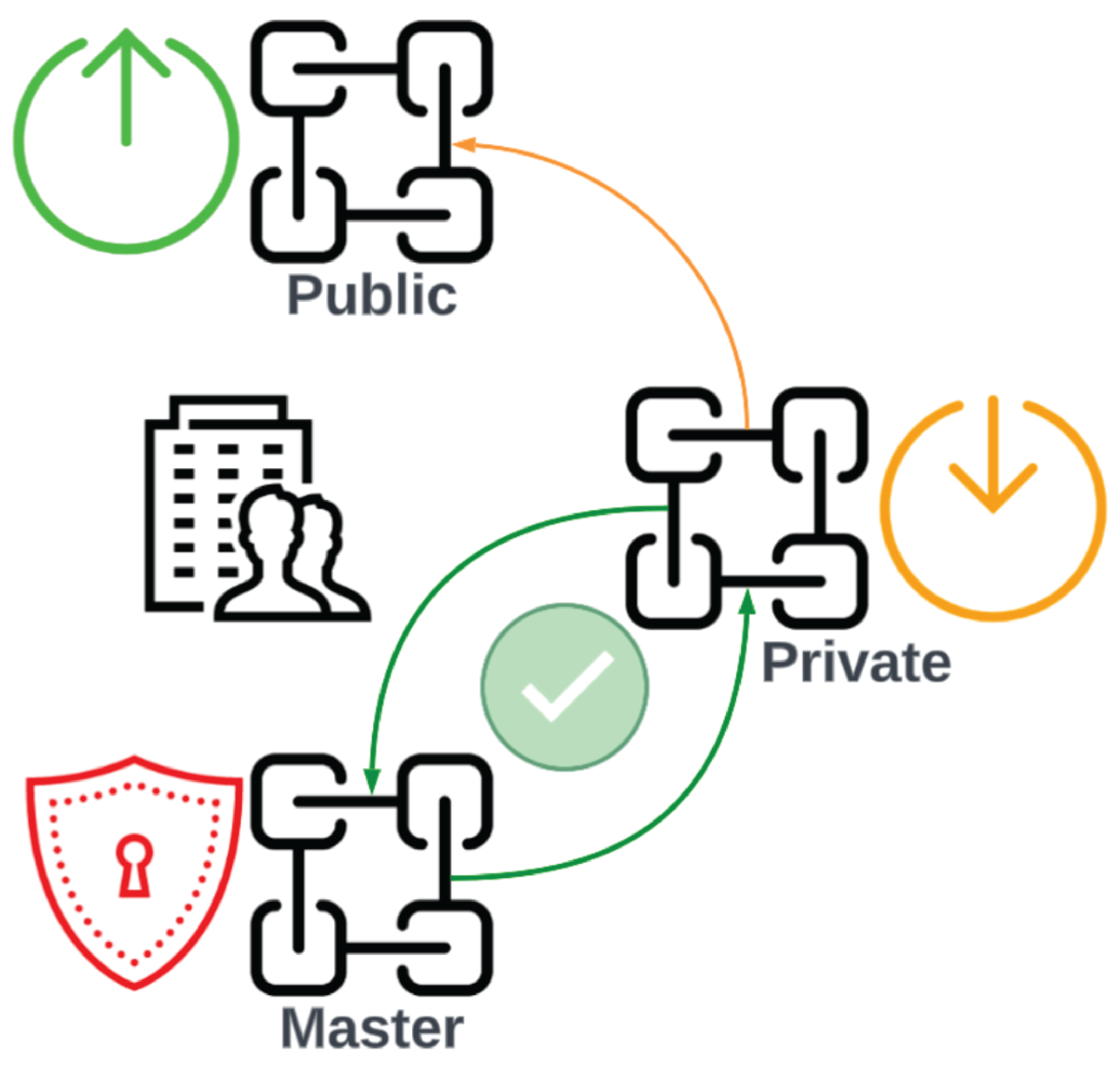
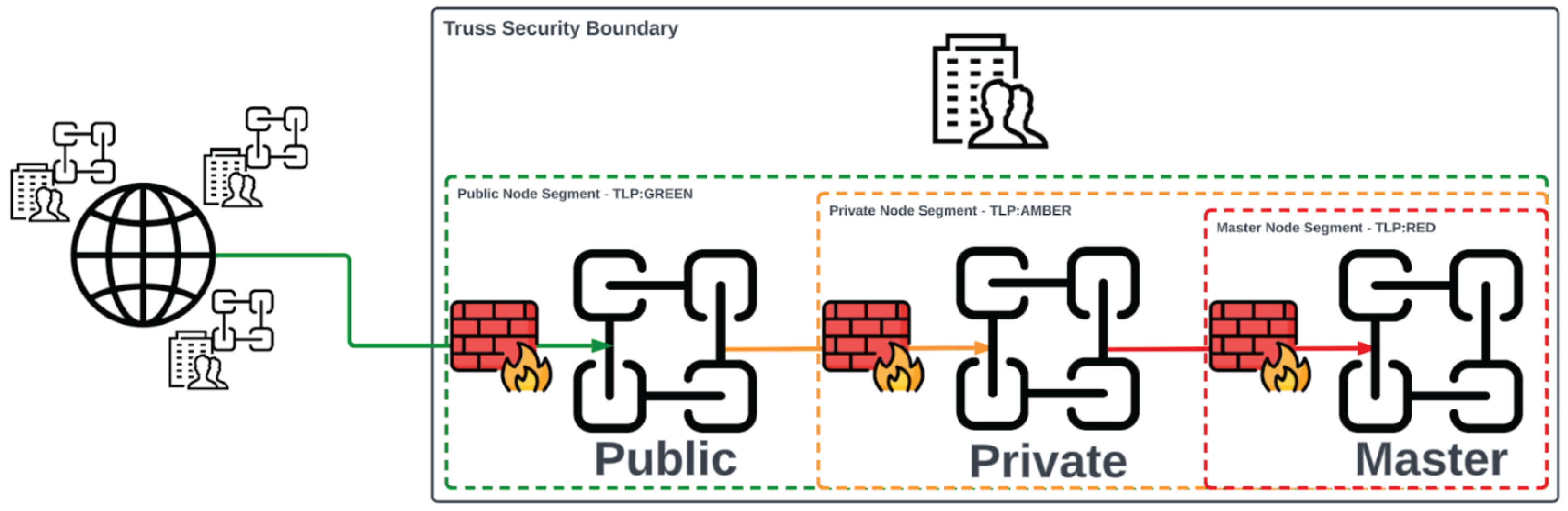
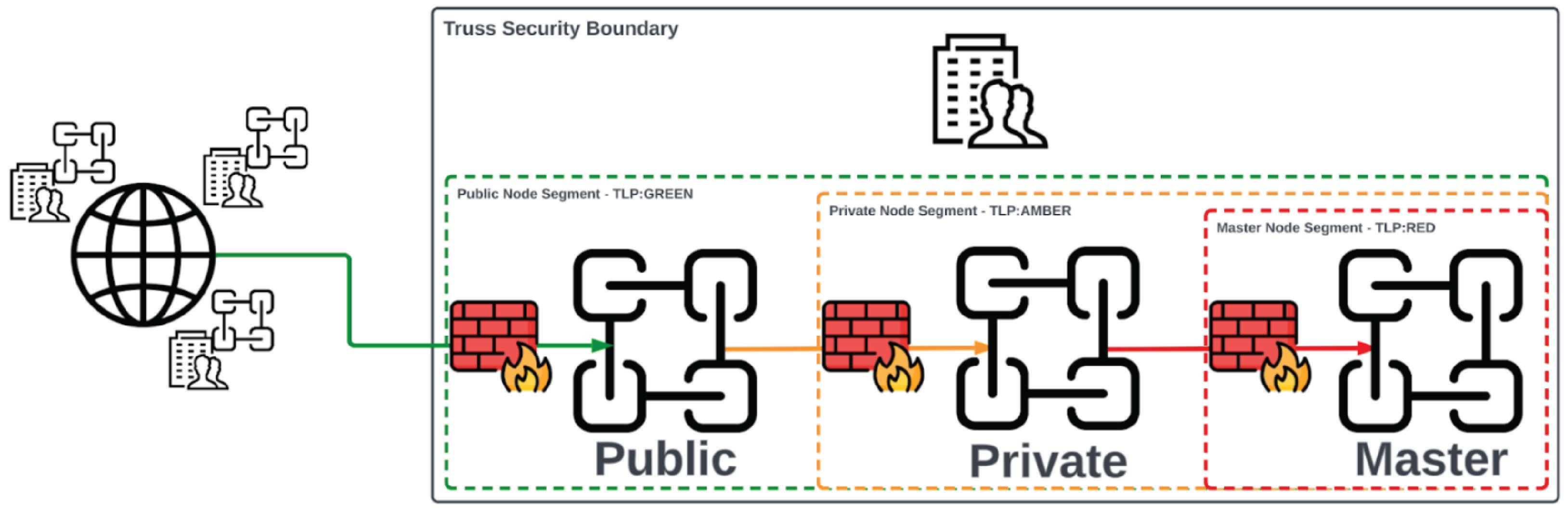
Organizations generally must manage large quantities of text-heavy security log data. This is in sharp contrast to the small and lightweight transactional data that is traditionally stored in public blockchains. In this situation, a hybrid blockchain can offer cost advantages compared to a fully public blockchain. By utilizing a private blockchain layer for internal or sensitive operations, organizations can reduce the computational and storage costs associated with public blockchain networks. A hybrid chain ecosystem supports the coexistence of internal private permissioned chains alongside a public permissionless chain. An organization implementing full Truss infrastructure might maintain two or more internal private blockchain nodes for log collection and threat intelligence ingestion. It would also interact with the public blockchain for reporting and disseminating threat data. In total, the three types of blockchains include the public Truss blockchain, a private blockchain, and finally a master blockchain (Figure 10).
Public Blockchain
The public chain is external to the organization. Data from the private chain is shared with the public chain via a customizable smart contract that can redact some or all of the internal or sensitive information contained within the private blockchain. This can allow Truss entities to share as much or as little data about a particular event as they feel comfortable. For example, a DAO may wish all information within their network to be fully transparent as this is a cornerstone of their operational philosophy, whereas a Fortune 100 enterprise may wish to share very little information as this could jeopardize their shareholder's confidence in protecting their intellectual property.
Private Blockchain
The private blockchain is used by the Truss entity as the production-ready security operations hub for monitoring and detecting all security events generated from the Truss entity's computational environment. The private nodes are hosted internally within the Truss entity's production environment and is not exposed to the internet. It is possible to maintain several unique nodes to assist with large log volumes and investigation requirements. The private blockchain could also replace a Security Information and Event Management (SIEM) appliance as the two share similar functionality.
Master Blockchain Nodes
The master blockchain is optional and is only used as an integrity check and a core source of truth for the Truss entity's security events recorded within the private blockchain nodes. The master node would be hosted under an additional layer of security from the production environment and from the private node. User access to the master node would be strictly controlled and external network access would be prohibited. Only isolated and heavily regulated service accounts would be allowed to interact with the master blockchain to ensure that the data contained within is uncompromised (Figure 11).
Private Chains
Sharing Cyber Threat Data
Selling Cyber Threat Data
Fueled by a growing number of security practitioners vying for the selling of the latest defensive measures, more knowledge will be shared within the ecosystem, resulting in a natural reduction in the number of sustainable malicious actors and the elimination of their offensive capabilities. Furthermore, the more exposed and unsanitized a Truss entity chooses to make its public blockchain, the more visibility analysts can achieve, resulting in more sophisticated detection and defensive measures being made available to the public.
Conclusion
Today's cyber attacks are highly decentralized, with multiple threat actors operating independent campaigns against multiple target sets. These attacks occur continuously and from nearly every country around the world. Yet, today's commercial cyber defense solutions are centralized data silos that require each security vendor to continually expand their data collection requirements. This expanding siloed data approach is simply unsustainable in keeping costs low and delivering timely security protections. Successful defense against these global decentralized attacks requires a decentralized security (DeSec) approach, one that is capable of providing authenticated transfer of real-time security data, to address key threats.
This paper argues that a hybrid blockchain, that combines elements from both public and private blockchains, provides the optimal DeSec architecture. A community-managed public blockchain hosts the security products, facilitating the integrity and trust of global security data and giving organizations access to the protection data they need to secure their environments. At the same time, a Utility Token supported by the public chain creates economic incentivization to perform and produce quality security services, data, and intelligence.
Internal private blockchains are used by organizations as production-ready security operation hubs for monitoring and detecting security events published to the public chain. Internal chains enable organizations to store their security data while offering a means to quickly share this data with the public. Through the configurable selling of their security data, the organizations themselves can begin to have their security teams become a profit center for the organization, while simultaneously allowing their data to strengthen the defenses and enhance the protections for the global security community.
All members of the DeSec community add to the collective intelligence and identification of cyber threats. Each member plays an active role in the global immune system by producing timely and relevant security data for an attack they witnessed. The global immune system incentivizes the early detection, response, and mitigation of cyberattacks by pushing the economic structure to the data producers and analytic creators. Purchasers of this data buy individual security products directly from the producers and analytic creators instead of from a large monolithic security platform. This reduces the need for organizations to facilitate large-scale in-house security operations and encourages a lower global security cost. Finally, the DeSec ecosystem facilitates the real-time distribution of attack data, allowing organizations to detect and mitigate active threat actor campaigns in real-time, instead of being required to wait for mitigations from their sole security provider.
References
The following references were used during the creation of this whitepaper. All attempts were made to ensure the citing of these sources were authentic and valid.
- BEC Attacks Increase by Astounding 84%. (2022, August 8). Abnormal. https://abnormalsecurity.com/blog/bec-attacks-increasing-new-research-shows
- Brown, R., & M Lee, R. (2021, January). 2021 SANS Cyber Threat Intelligence (CTI) Survey. ThreatQ. Retrieved June 11, 2023, from https://www.threatq.com/documentation/Survey_CTI-2021_ThreatQuotient.pdf
- Cost of a data breach 2022. (n.d.). IBM. https://www.ibm.com/reports/data-breach
- Cybercrimemag. (2023, April 15). Cybersecurity Jobs Report: 3.5 Million Unfilled Positions In 2025. Cybercrime Magazine. https://cybersecurityventures.com/jobs/
- CyberDB. (2018, May 7). USA Cyber Security Companies | CyberDB. https://www.cyberdb.co/database/usa/page/2/
- DavidPur, N. (n.d.). Which Countries are Most Dangerous? Cyber Attack Origin – by Country. https://blog.cyberproof.com/blog/which-countries-are-most-dangerous
- De Vries, R. (2022, August 3). What are the real costs of a security incident? | Tales from a Security Professional. Medium. https://tales-from-a-security-professional.com/what-are-the-real-costs-of-a-security-incident-dec0d090281f
- Gatefy. (2021). Which countries are most targeted by hackers? Gatefy. https://gatefy.com/blog/which-countries-are-most-targeted-hackers/
- Huang, K. (2023, May 4). The Devastating Business Impacts of a Cyber Breach. Harvard Business Review. https://hbr.org/2023/05/the-devastating-business-impacts-of-a-cyber-breach
- Lemos, R. (2022, September 30). Cybercriminals See Allure in BEC Attacks Over Ransomware. Dark Reading. https://www.darkreading.com/threat-intelligence/cybercriminals-see-allure-bec-attacks-ransomware
- Mandiant. (n.d.). Mandiant Security Effectiveness Report: DEEP DIVE INTO CYBER REALITY. Mandiant. https://www.mandiant.com/resources/security-effectiveness-2020-deep-dive-into-cyber-security-reality
- Nibley, B. (2021, December 22). What Is a Utility Token? SoFi Learn. Retrieved June 11, 2023, from https://www.sofi.com/learn/content/what-is-a-utility-token/
- Oltsik, J., & Lundell, B. (2021, July). The Life and Times of Cybersecurity Professionals 2021 Vol 5. issa.org. Retrieved June 11, 2023, from https://www.issa.org/wp-content/uploads/2021/07/ESG-ISSA-Research-Report-Life-of-Cybersecurity-Professionals-Jul-2021.pdf
- Pandemic Cyber Crime, By the Numbers. (n.d.). Pandemic Cyber Crime, by the Numbers. https://www.cyberark.com/resources/blog/pandemic-cyber-crime-by-the-numbers
- PurpleSec. (2023, February 22). 2023 Cyber Security Statistics: The Ultimate List Of Stats, Data & Trends | PurpleSec. https://purplesec.us/resources/cyber-security-statistics/#Ransomware
- Roesch, M. (1999). SNORT - lightweight intrusion detection for networks. https://www.usenix.org/. Retrieved June 11, 2023, from https://www.usenix.org/legacy/publications/library/proceedings/lisa99/full_papers/roesch/roesch.pdf
- Security Market Size, Share & Trends Analysis Report By System (Video Surveillance, Access Control Systems), By End-use (Commercial, Industrial), By Service, By Region, And Segment Forecasts, 2023 - 2030. (n.d.). https://www.grandviewresearch.com/industry-analysis/security-market
- Shirky, C. (2008). Here Comes Everybody - The Power of Organizing without Organizations. Google Books. Retrieved June 11, 2023, from https://books.google.com/books?hl=en&lr=&id=mafZyckH_bAC&oi=fnd&pg=PA1&dq=shirky+2008+here+comes+everybody+&ots=HLpadLTBE3&sig=FxuGnd_ZJp5rUB8TweMQFVOO3Cg#v=onepage&q=shirky%202008%20here%20comes%20everybody&f=false
- Traffic Light Protocol (TLP) Definitions and Usage | CISA. (2022, August 16). Cybersecurity and Infrastructure Security Agency CISA. https://www.cisa.gov/news-events/news/traffic-light-protocol-tlp-definitions-and-usage
- Unit 42. (2022, March 24). 2022 Unit 42 Ransomware Threat Report Highlights: Ransomware Remains a Headliner. Unit 42. https://unit42.paloaltonetworks.com/2022-ransomware-threat-report-highlights/
- What are smart contracts on blockchain? | IBM. (n.d.). https://www.ibm.com/topics/smart-contracts
- Zrahia, A. (2018, December 18). Threat intelligence sharing between cybersecurity vendors: Network, dyadic, and agent views. Journal of Cybersecurity, 4(1). https://doi.org/10.1093/cybsec/tyy008
- Stoltz, R. (2021). Cyber Security Job Outlook in 2023. NEIT. https://www.neit.edu/blog/cyber-security-job-outlook
- Cybersecurity workforce estimate by country 2022 | Statista. (2023b, April 14). Statista. https://www.statista.com/statistics/1172449/worldwide-cybersecurity-workforce/
- 2023 Data Breach Investigations report. (n.d.). Verizon Business. https://www.verizon.com/business/resources/reports/dbir/